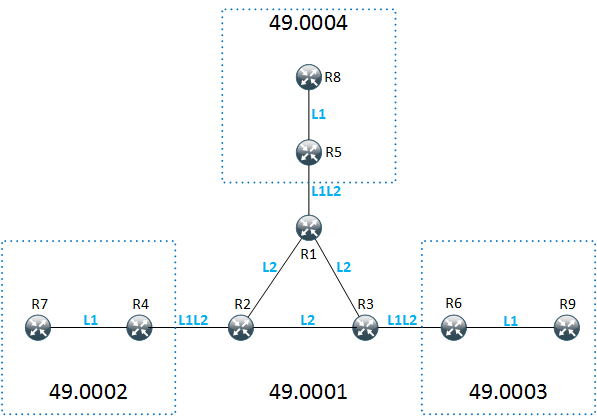
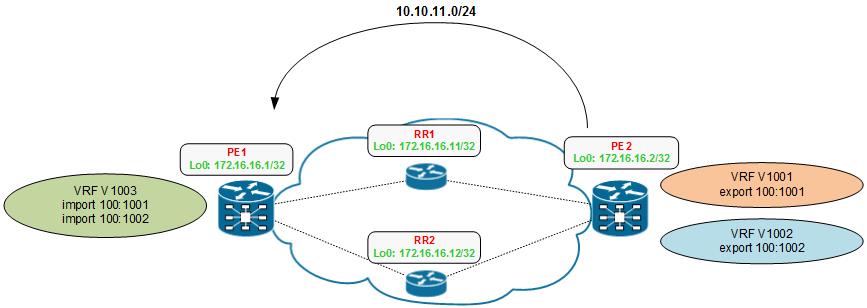
Traceroute/mtr in MPLS
This post is not meant to be an introduction to traceroute in MPLS. There are many good resources on this topic already.
It is meant to provide a quick reference how a traceroute should look like in a healthy network and how different features might influence the outputs. Most of …
more ...