Here are my notes about how IS-IS deals with authentication. I'll be working on a simple network consisting of IOS XE, IOS XR and Junos based routers.
Here is reference diagram:
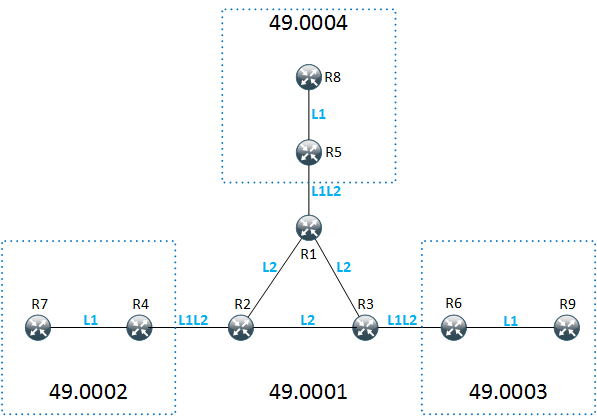
Some initial checks
First, I'll start off by verifying IS-IS adjacencies on R6.
R6#sh isis neighbors
Tag 1:
System Id Type Interface IP Address State Holdtime Circuit Id
R3 L2 Gi1 10.3.6.3 UP 22 02
R9 L1 Gi2 10.6.9.9 UP 25 01
I'll check routing table on R9, too.
R9#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is 10.6.9.6 to network 0.0.0.0
i*L1 0.0.0.0/0 [115/10] via 10.6.9.6, 00:03:00, GigabitEthernet1
9.0.0.0/32 is subnetted, 1 subnets
C 9.9.9.9 is directly connected, Loopback0
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
i L1 10.3.6.0/24 [115/20] via 10.6.9.6, 00:24:00, GigabitEthernet1
C 10.6.9.0/24 is directly connected, GigabitEthernet1
L 10.6.9.9/32 is directly connected, GigabitEthernet1
So far, so good. R6 is L1L2 router, so it sets ATT bit on LSP it generates.
I wasn't able to find an operational command to verify IS-IS authentication status both on IOS XE and XR
- IS-IS, similar to OSPF uses either plain text or MD5 authentication
- It uses Authentication TLV #10 to carry these information
- Authentication of protocol messages can be done on a per message type basis
- IS-IS, just like OSPF uses fightback
- IS-IS, unlike OSPF doesn't carry Cryptographic Sequence Numbers
- It is possible to change keys without disrupting IS-IS adjacency
Comments
comments powered by Disqus