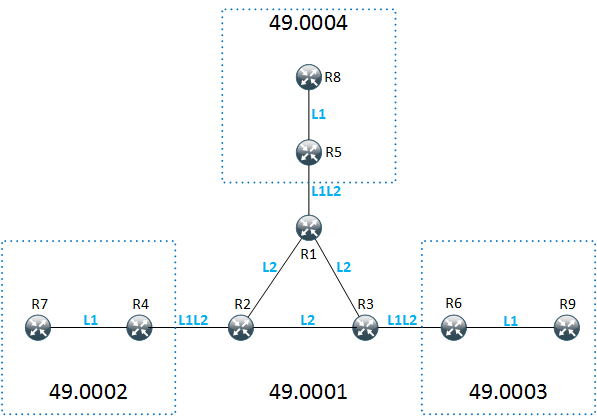
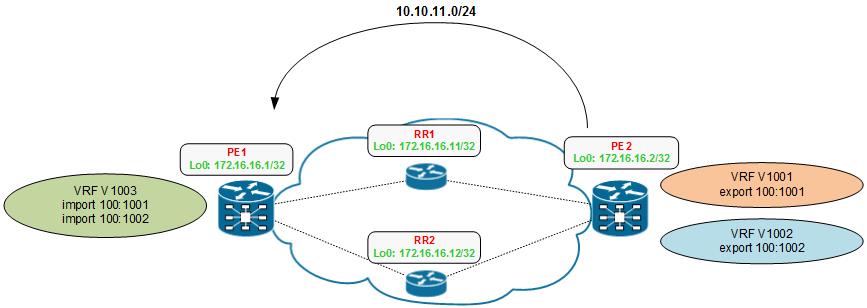
L2 protocol tunelling (ASR920)
Sometimes when we purchase a L2 service from a service provider, we need to have our L2 protocols tunneled.
ASR920 platform gives the operator three option to choose from:
l2protocol tunnell2protool peerl2protocol forward
Although I've been working with ASR920s for a while, I didn't have the time to …
more ...